Industrial Visual Inspection – Defect and Anomaly Detection in Manufacturing
Inside this article:
In industrial production, the detection of defects and anomalies is crucial for maintaining quality standards. In many cases, human inspectors are used to examining products as they come off the production line. However, with the advent of machine learning and artificial intelligence, it is now possible to use custom models to detect defects and anomalies in images. In this blog post, we will explore the use of machine learning in visual inspection and discuss some of the benefits it offers for manufacturers. We will look at real-world use cases from different industries and see why AI-based visual anomaly detection is becoming increasingly popular in modern manufacturing facilities.
Traditional Inspection on Production Lines
Since the beginning of the industrial age, the manufacturers have been using different techniques to monitor the quality of the processes and products on the assembly line. These techniques - until relatively recently - would have to involve humans. But with gradually increasing manufacturing volume and growing demand, it naturally has been becoming harder and harder to monitor the quality and detect issues on the assembly line. The inspectors would find it hard to deal with such a great deal of products, which would affect the results. The monotonousness of such a task doesn’t help, causing fatigue and increasing the probability of errors.
The Introduction of Automation for Anomaly Detection
Automation was a breakthrough for the manufacturers, allowing them to increase their production volume massively without compromising quality standards. Suddenly, they were able to automate a big part of the manufacturing process, including the most error-prone tasks, like defect and anomaly detection. But artificial intelligence was a real game-changer, replacing programmed, poorly adaptive with flexible, self-learning, and self-improving ones.
Machine Learning and Computer Vision to Aid Anomaly Detection
Visual monitoring in its most traditional form has many limitations – with the bigger one being a relatively slow reaction. Once the machine detects an anomaly or defect, it can trigger an automatic reaction, whereas, without AI, these actions have to be carried out manually. In manufacturing, where every second counts, it’s counterproductive. Particularly in Pharma, one relatively small issue can affect the whole batch, causing massive losses.
Another thing is the consistency of quality assurance. With the automated tools, all data regarding the defects and anomalies stays in the system.The machine can draw conclusions from it, continuously improving its detection capabilities. Whereas in the case of the traditional defect and anomaly detection method, the effectiveness of quality monitoring may drastically fall with any personnel change – and that means costs.
AI-based Computer Vision solves these problems, improving quality control and quality assurance. How exactly? Let’s get into that.
Can AI-Based Computer Vision Detect Defects and Identify Anomalies?
Artificial intelligence imitates human behavior – and as its branch, computer vision reproduces human capability to interpret the image. The technology draws from the complexity of the human vision system, imitating its way of processing visual information. While the mystery of capturing images was solved hundreds of years ago (and sealed with the invention of the camera), interpreting it has always been the tough part. With artificial intelligence, it finally became possible.

In the case of computer vision, an eye is replaced with the sensing device and the visual cortex - with an interpreting device powered by the machine learning algorithm. Trained with large image datasets, the deep learning model can interpret the content of a given image. That mechanism is used in manufacturing for defect and anomaly detection.

Fed with image samples of the impeccable products that fulfill all the quality requirements, the deep learning model constitutes its own logic, learning to identify different types of flaws. The image captured by the device is evaluated on its basis, and if it doesn’t match, the defect is immediately flagged. Developers can draw from different methods, creating generative anomaly detection algorithms like Bayesian networks, Recurrent Neural Networks (RNN), Convolutional Neural Networks (CNN), GAN, or Variational Autoencoder.
In the most common scenario, algorithms classify the products as defective or not defective. Models can also be trained with supervised learning to classify defects based on their severity, type, or status. That enables creating more sophisticated mechanisms of automatically triggered reactions and gathering detailed data.
Applying Machine Learning to Quality Assurance – Industry Use Cases
The increasingly competitive entrepreneurial landscape makes companies constantly improve the quality of their products, and AI-based automated tools can be an invaluable support in this process. With computer vision, they can evaluate the quality of their products more efficiently without engaging an additional workforce or losing consistency.
The use cases below prove the versatility of this technology. Let’s take a closer look at defect and anomaly detection applications across industries.
Visual Inspection in Pharma and Life Sciences
Cross-contamination of the cell lines is one of the most common risks the pharmaceutic and scientific labs face on a daily basis. Sometimes it takes just one dropper to be accidentally reused for the contamination to occur. The outcomes may be costly since they can have a negative impact on lab research or even make the pharmaceutical product unusable.
Keeping the quality standards and training, the pharmaceutical companies can reduce the probability of cross-contamination, but it still can happen - and image processing with deep learning can help identify it at the early stage. The deep neural network can detect small morphology changes in cells, protecting pharma companies and labs from having their results adulterated. For instance, this case study from ATM (Annals of Translational Medicine) proves that neural networks (specifically, a BCNN) can achieve close-to-100% accuracy in identifying cell lines.
For biotech companies, visual inspection is applied to monitor cell cultures, identify cross-contamination, and track morphological changes. Deep learning models can detect such changes at the stage when they are not yet visible to the human eye (through microscopes), making it possible to take preventive measures on time and avoid costly consequences. Dedicated ML software analyzes images of cells and provides reports with valuable insights to help clients improve the efficiency of their research.
Visual inspections help the pharmaceutical companies control the packaging, too. Pharma companies (particularly those in European Union) are subject to strict norms and regulations regarding the containers for their pharmaceutical products. Most products require airtight closure and the usage of specific materials. At the same time, any defect in packaging can affect the efficiency of the medication and its shelf life. With computer vision, such issues can be detected at an early stage.
Detecting Defects in Semiconductor Manufacturing Processes
Visual inspection can help companies from various industries keep an eye on the quality of the products themselves, but also on their state. They can use image processing for monitoring semiconductor manufacturing processes such as cleaning, film deposition, etching, exposure, implantation, resist coating, implantation of impurities, or heat processing. The models can detect anomalies in wafer levels and automate such processes as pre-place inspection.
The rule is the same – the visual inspection system based on a deep learning algorithm gets trained with images of good quality products after each semiconductor process and learns to identify defects. A good image processing device is the key in this case since the defects may be hardly detectable.
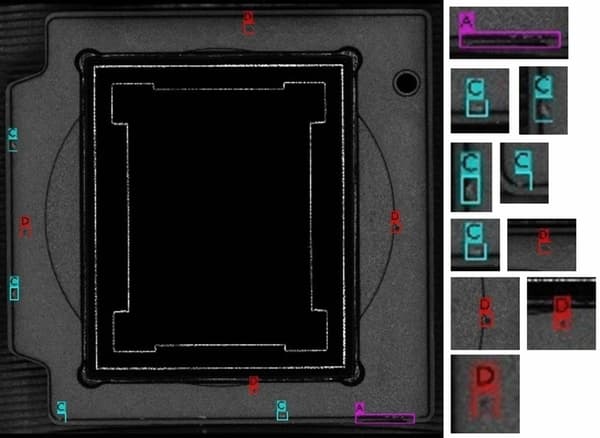
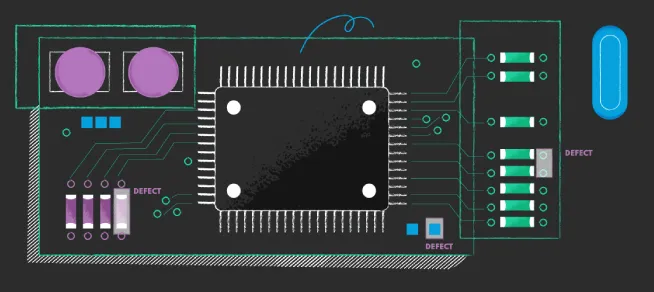
Quality Assurance for Electronics Manufacturers
The capabilities of visual inspection are particularly impressive when it comes to electronics manufacturing. Well-trained models can detect even the tiniest defects that are barely visible to the human eye. Companies use deep learning techniques to find potential anomalies in microchips, transformers, monitors, CPUs, and other manufactured parts - many of them really tiny.
To keep the imaging non-destructive, the electronic manufacturers tend to draw information regarding defects from CT scans. Using X-ray tomography, they can generate radiographic projections of the manufactured elements. The generated image is later translated by the algorithm to its 3-d representation.
Due to the complexity of the elements, it’s essential for the manufacturers to narrow the scope of analysis to the parts susceptible to defects or damage. Otherwise, it will be challenging to appropriately train the deep learning network for defect/anomaly detection.
Visual Quality Inspection in Chemicals Production
Even though at first glance, visual inspection methods may not seem the most suitable for evaluating the quality of chemical manufacturing, they are actually proven to work. In typical chemical manufacture, the samples would get sent into the lab to be tested manually. This process is neither efficient nor accurate, as a few samples may not represent the quality of the whole batch. Meanwhile, testing every product on the chemical production line is far from cost-effective.
The manufacturers can evaluate their quality in a faster, cheaper way, using computer vision. The mechanism of visual quality inspection is similar to the case of solid objects – the model gets trained with the images of chemical products that fulfill quality standards and classifies those on the assembly line accordingly. Computer vision can detect anomalies based on the substance’s color, stratification, or physical state. If the product is clumped, oxidized, or layered, it can be automatically separated from the good ones and redirected from the production line.
Obviously, this method has some limitations since some defects in chemical substances are undetectable. However, a visual inspection can be an added value to the quality assurance system applied by the chemical manufacturer. You can also read about chemical supply chain here.
Off-The-Shelf Visual Inspection Systems vs. Custom Machine Learning Models
While there are quite some off-the-shelf visual inspection systems available on the market, many companies still decide to stick to custom machine learning models. The reason is simple – since off-the-shelf solutions are made to work for different companies, they enforce some compromises.
Even if they are flexible to a certain extent, there are limits that can sabotage the company’s business growth. For instance, the users may not be able to train the system using their own training data set, being forced to use the inbuilt databases. If their product and its features are unique, such a solution may not be enough to perform anomaly detection in a throughway.
Choosing to develop a custom machine learning model, the companies can adjust its type to the specifics of the task (take the cell line inspection described above, for which the BCNN has proven to deliver the most accurate results). With their own model, they can also extract regions of interest for increased accuracy, while off-the-shelf systems usually don’t offer such a possibility. As a result, those who pick custom anomaly detection models over ready-made solutions often enjoy more satisfactory outcomes.
The Benefits of AI-Based Visual Anomaly Detection in Manufacturing
AI is revolutionizing the manufacturing sector in many ways bringing numerous benefits. With AI-based visual inspection, the manufacturers can reduce their operational costs by:
- preventing downtimes with predictive maintenance
- reducing the workforce demand
- offloading the quality inspectors and delegating them to more demanding tasks
- reducing the number of returns and complaints
At the same time, they can improve customer satisfaction and enhance the company’s reputation. Less defective products delivered to the market obviously equals better satisfaction rates.
Would you like to take advantage of these benefits? Reach out to us to tell us more about the specifics of your industry and products; as an AI software development company, we might be able to help!
The Future of Efficient Manufacturing and Advanced Deep Learning for Anomaly Detection Model
Widespread adoption of anomaly detection methods based on deep learning in quality assurance is inevitable. The ever-growing competition on the market, as well as the need to meet the consumers’ expectations, will force the manufacturers to look for new ways to optimize their production lines. Applying machine learning algorithms to visual inspection tasks is one of those – it’s a move that can save millions of Euros or Dollars for big companies and make the production process more efficient.
Anomaly detection will undoubtedly shape the future of many industries, making our lives easier and healthier. After all, who wouldn’t want to receive a product that underwent a thorough quality check?
If you’re looking for a dedicated partner to help you develop custom models for computer vision and monitoring production lines, look no further and contact us today. We will be more than happy to help you take your business to the next level!